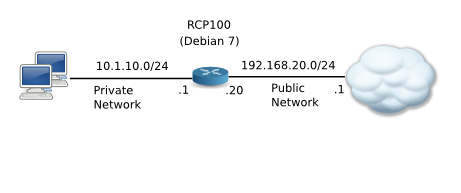
Firejail is a SUID sandbox program that reduces the risk of security breaches by restricting the running environment of untrusted applications using Linux namespaces. It allows a process and all its descendants to have their own private view of the globally shared kernel resources, such as the network stack, process table, mount table.
Started as a simple sandbox for Mozilla Firefox, Firejail was expanded to work on any type of executable, such as servers, graphic programs, and even as login shell.
The program is written in C and only needs libc and POSIX threads (libpthreads), available by default on any Linux platform. The download page provides source code (./configure && make && sudo make install), deb (dpkg -i firejail.deb) and rpm (rpm -i firejail.rpm) packages. Once installed, you can start a program in sandbox as:
$ firejail [options] program and arguments
Example:
$ firejail --debug firefox
Default sandbox
To login into a Firejail sandbox, you need to set /usr/bin/firejail as user shell in /etc/passwd. You can change the shell for an existing user with chsh command:
# chsh --shell /usr/bin/firejail
Another option is to define the shell when the user account is created:
# adduser --shell /usr/bin/firejail username
Below is a ssh login session into a sandboxed account:
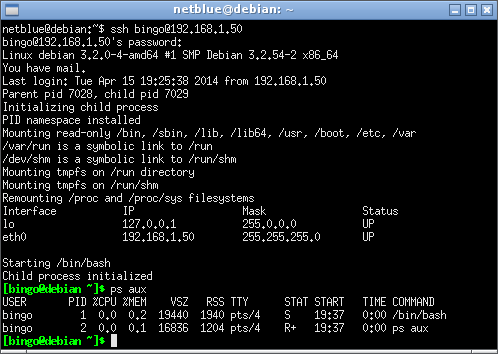
SSH login into a default Firejail sandbox
Continue reading →